Custom Event Sinks
From Build 2026-01-06 the IoT Gateway now supports configuration of custom Event Sinks in the gateway.config file. On the TAG Neuron, the contents of this file is editable, via the corresponding data source. From the Sources & Nodes menu in the administrative panel, the data source Gateway configuration now contains a new node called EventSinks:

Adding custom event sinks
By selecting the EventSinks node, and pressing the Add button, you can add new event sinks. The options available depend on what services are hosted on the Neuron:
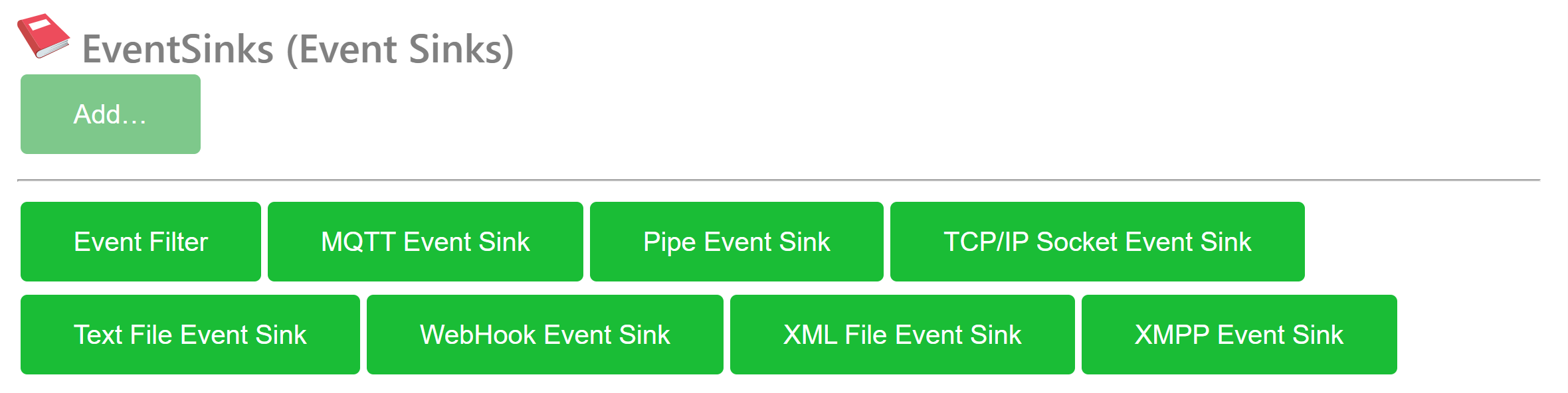
Default Event Sink Types
The following event sink types are available by default, at the time of writing:
Event Filter allows you to filter out a subset of events of interest. The Event Filter sink then passes it on to child-sinks, which propagate them in accordance with their instructions.
MQTT Event Sink propagate incoming events to a topic on an MQTT broker.
Pipe Event Sink forwards events to an operating system Pipe, allowing another process on the machine access to the events.
TCP/IP Socket Event Sink sends the logged events via TCP/IP to a remote machine.
Text File Event Sink stores events in text files. By including date and time tags in the file name, a sequence of files can be generated. The event sink also automatically delete old files.
WebHook Event Sink forwards events to an external source using
POST. The protocol used depends on the URI scheme used by the Callback URI. The WebHook Event Sink can also collect and group events together, for easier processing on the recipient side.XML File Event Sink records events into XML files. Date and Time tags in the filename allow you to create a sequence of XML files generated. Old files are automatically deleted.
XMPP Event Sink sends logged events to an XMPP recipient. Child Nodes
Testing WebHooks
When developing server-to-server applications, it is important to be able to test webhooks without leaking sensitive or private information. To avoid having to use 3rd party services, such as webhook.site a new package has been made available containing a service that can be installed on any Neuron®, that allows you to view incoming POST requests in a similar fashion.
Installable Package
The Web-Hook Tester service has been made into a package that can be downloaded and installed on any TAG Neuron. If your Neuron is connected to the TAG Neuron network, you can install the package using the following information:
| Package information | |
|---|---|
| Package | TAG.WebHookTester.package |
| Installation key | Mb9pim8FTjHBnju2f2ZVNHBRbOG3VHhM7iBn26mgcvc/uwjouWjHEF0OmcC/noKEuZAOWZY6Ka4A4abb4fc2a2596e04f047400e3218dcd2 |
| Repository | WebHookTester repository at GitHub |
Installing the package via the administrative console (Chat Admin), can be done using the following command:
install nobackup TAG.WebHookTester.package Mb9pim8FTjHBnju2f2ZVNHBRbOG3VHhM7iBn26mgcvc/uwjouWjHEF0OmcC/noKEuZAOWZY6Ka4A4abb4fc2a2596e04f047400e3218dcd2
Starting service
The WebHook tester service appears in the administrative portal, in the Software section:

Pressing it, opens the following page: https://lab.tagroot.io/WebHookTester/Show.md
Note: This page does not require client authentication, and can be used anonymously.
Note 2: You can also use the script prompt to make custom POST calls to the page. This requires elevated privileges however, and cannot be done anonymously.
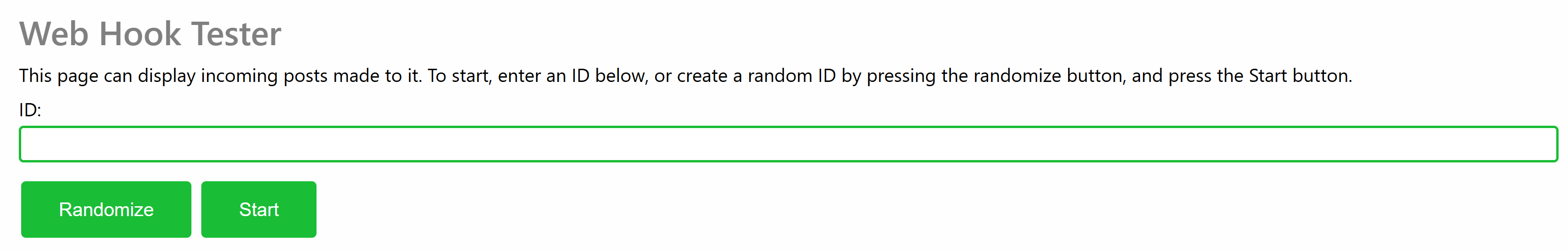
Creating a Page
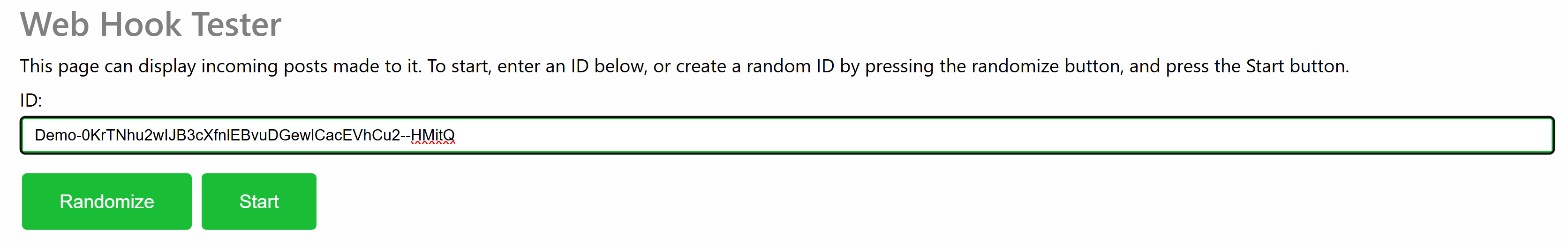
Enter an ID and press the Start button to create a new page you can POST to. Since the service can be accessible by anyone, use an ID that is difficult to guess, if you do not want others to get easy access to the information. Press the Randomize button to create a random ID. You can customize the random ID to remember the purpose of the page, if you have multiple pages open.
Test Page
When you press the Start button, a new page is opened. It contains instructions how you can POST to the page:
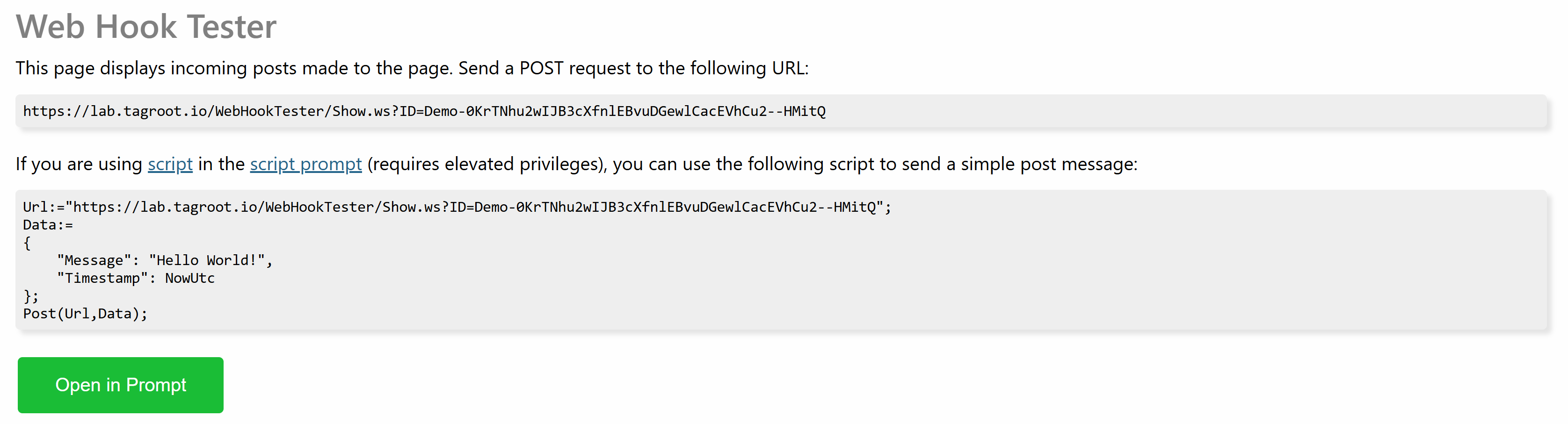
Use the URL presented to POST to the page. If you want to test a back-end service integration, this is the URL you provide as a webhook callback URL. Any POST made to this URL will be displayed on the page.
Note: Nothing is saved or persisted on the page. The page does not remember previous POSTs, so if you refresh the page you loose the information on the page.
Note 2: Make sure to differentiate between the URL of the page (which points to a resource with extension .md) and the URL to POST to (which points to a resource with extension .ws).
Incoming POSTs
As soon as an incoming POST is made, it is displayed on the page as follows. It displays the time of the event, any HTTP headers in the request, together with a textual representation of the payload (if content is text-based), as well as the binary payload, BASE64-encoded. Each POST is presented in its own SECTION tag on the page.
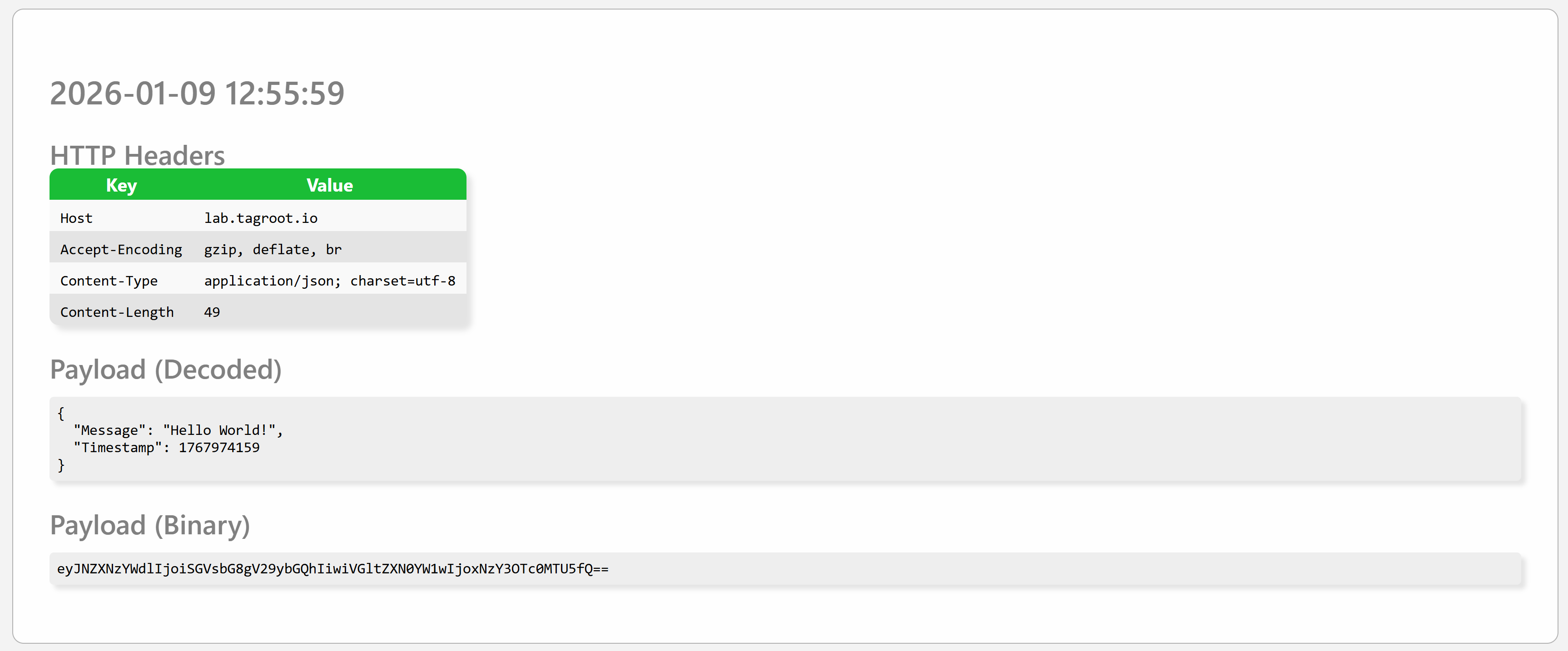
Responses
The response to a POST call to the resource will be a JSON object with one property called Forwarded, which indicate the number of pages the information was forwarded to. If this number is 0, the page has closed or lost contact with the Neuron. Example:
{
"Forwarded":1
}
Tunneling POST request over XMPP
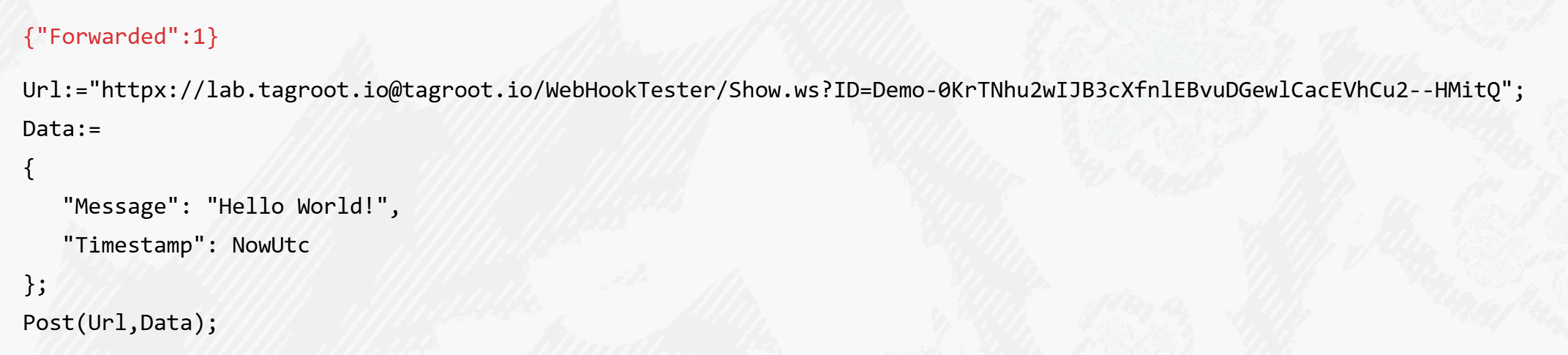
As the Neuron is connected to the XMPP network as well, since it is hosted on the IoT Gateway, the POST request can be tunneled over the XMPP network using the httpx:// URI scheme. This permits you to do callbacks to local development machines, or machines not accessible via the Internet.
To achieve this, you need to perform the call from another instance hosted on the IoT Gateway. It can be the IoT Gateway itself, Lil’Sis’ or another instance of the TAG Neuron, including a development version on a local machine. You replace the https scheme in the URI with the httpx URI scheme, and replace the host with the JID of the recipient. For the call to succeed, the sender and receiver need to be friends, i.e. have approved presence subscriptions, for the call over XMPP to be possible.
This can be easily tested using the script prompt:
Note: Any software using the Waher.Content Internet Content-Type abstraction, and the InternetContent content access methods, together with the Waher.Networking.XMPP.HTTPX library (containing the httpx URI scheme definition) will automatically support httpx URIs.
Note 2: Since the QuickLogin API and RemoteLogin API are both hosted on the TAG Neuron®, you can register httpx callback URIs with these APIs. This makes it possible to host the recipient service behind a firewall, as long as it supports the HTTP over XMPP protocol
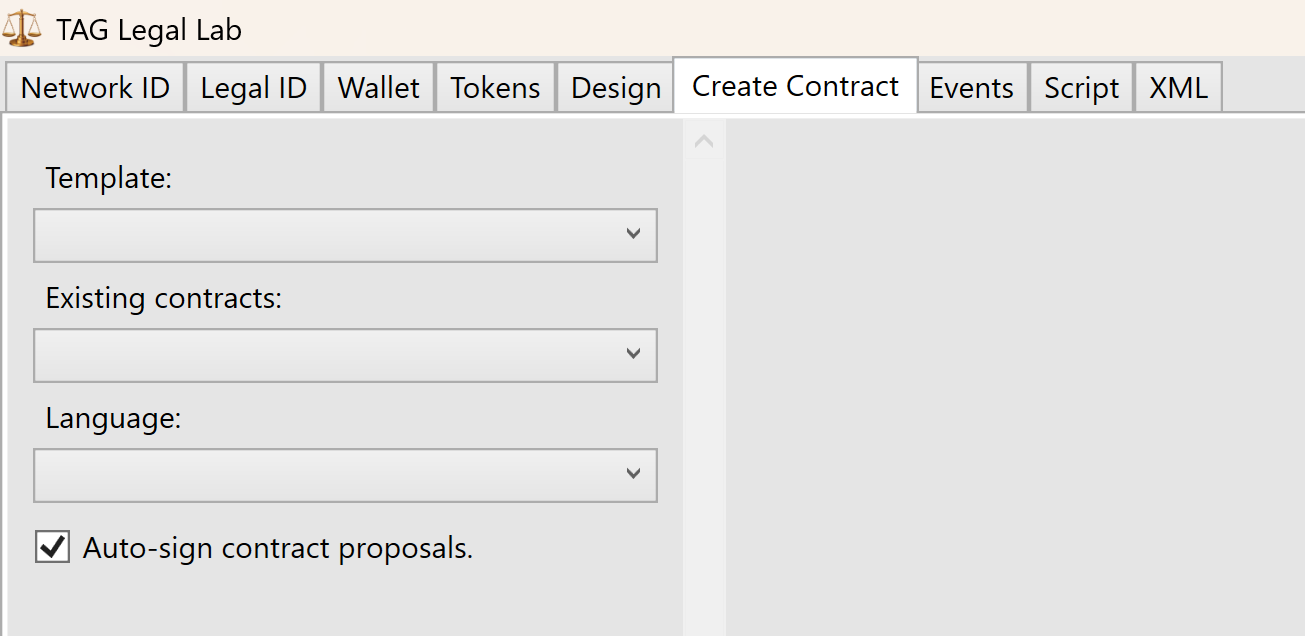
Auto-signing contract proposals using LegalLab
It is now possible to let LegalLab auto-sign contract proposals for you, simplifying often occurring tasks during development. You enable this feature by checking the “Auto-sign contract proposals” checkbox in the Create Contract tab. The feature is only available when LegalLab is connected. If this checkbox is enabled when a contract proposal is received, the contract will be automatically loaded and presented, and LegalLab will automatically sign the contract for the proposed role.
Killing a State Machine
If a state-machine associated with a token or set of tokens misbehaves, and needs to be stopped, an operator of Neuro-Features on the Neuron® that hosts the state-machine can kill it. This does not destroy the token or tokens associated with the state-machine, it just stops the state-machine. The event is also appropriately logged, with information about who took the responsibility to kill the machine.
In order to be able to kill a state machine, the operator needs to fullfil the following requirements:
- Be an operator on the Neuron hosting the state-machine (i.e. have an administrative account on the Neuron).
- Have a Digital ID associated with the account.
- Have sufficient access rights to administer Neuro-Features. (This means, having the
Admin.Notarius.NeuroFeaturesprivilege associated with one of its roles.) - Digitally sign an approval of the killing of the machine, where the user affirms to reviewing the token and taking the responsibility of killing the state-machine.
Accessing the Token
To access available tokens on the Neuron, go to the Neuro-Features section in the administrative portal:
Find the corresponding token, and open it by clicking on its ID. A link of the following type is opened:
https://DOMAIN/NeuroFeature.md?ID=TOKEN_ID
If you know the Token ID, you can open the page directly by replacing TOKEN_ID in the URL above with the correct Token ID. If you don’t know the Token ID, but you know the ID of the smart contract that created the token, you can use the script prompt, to find the Token ID, using the following SELECT statement:
select
top 1 TokenId
from
NeuroFeatureTokens
where
CreationContract=CONTRACT_ID
Killing the state machine
Once the Current State part of the Neuro-Feature page has loaded, it will present a Kill Machine button, if the token has an associated state-machine.

Press this button to open a new page where you can kill the machine. The page has the following URL. If you have the Token ID already, and cannot open the Neuro-Feature page associated with the token for some reason, you can enter this URL directly into the broker, replacing TOKEN_ID with the corresponding Token ID:
https://DOMAIN/KillMachine.md?ID=TOKEN_ID
The page that opens is simple and informs the user they need to approve the operation using their Digital ID, and that they will be responsible for the action:
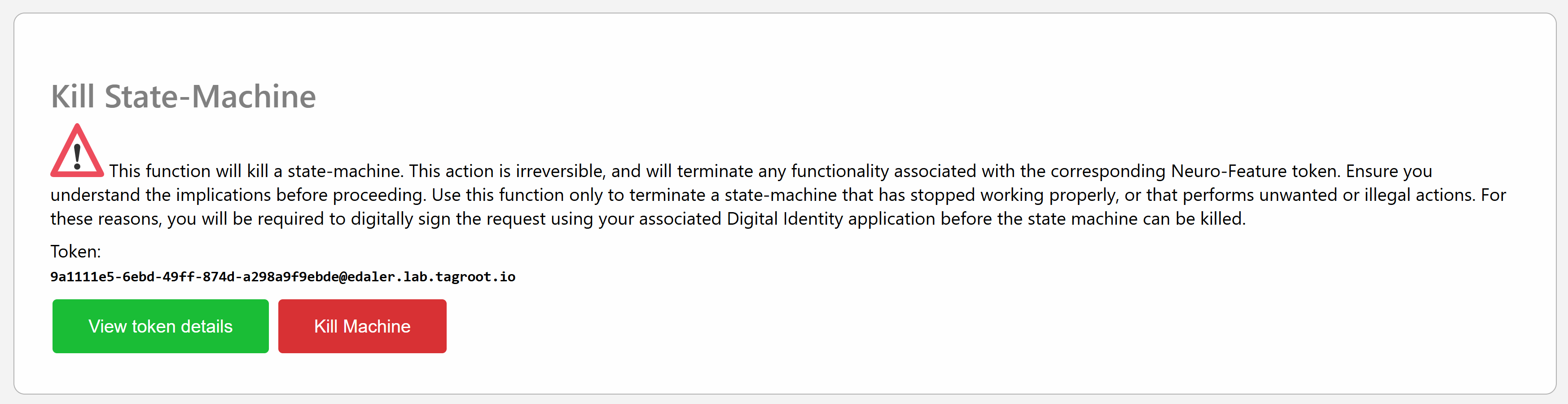
Press the Kill Machine button to initiate the process by sending a petition to the Digital Identity of the currently logged in user:
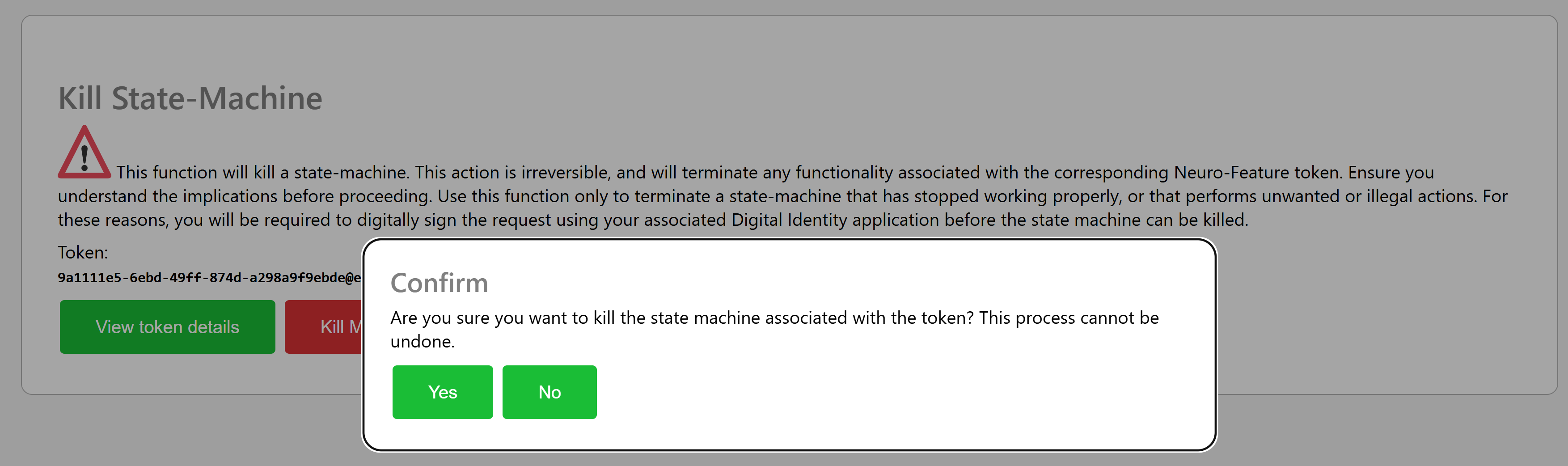
If a Legal Identity is associated with your account you will receive an acknowledgement that a petition has been sent.

You will see this petition in your Digital ID app, as follows:
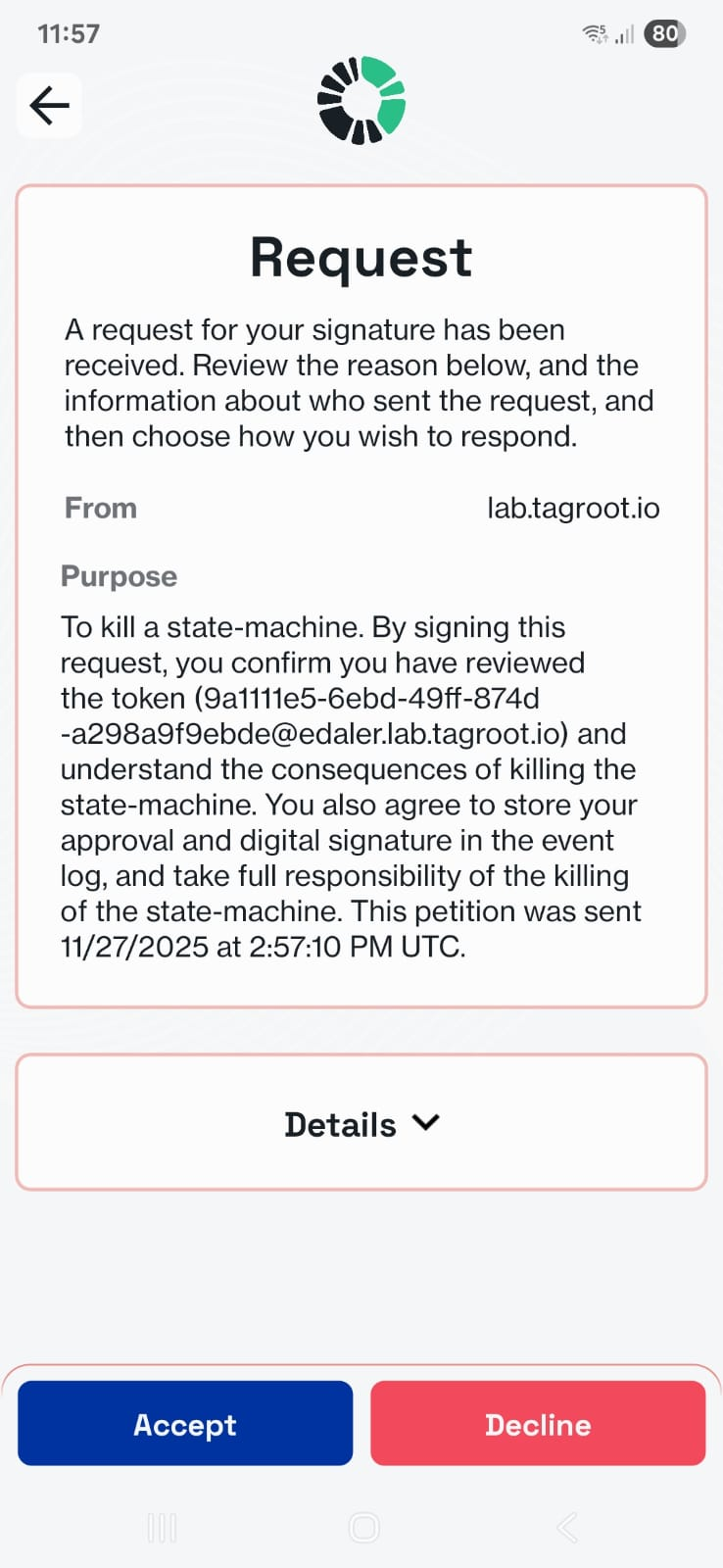
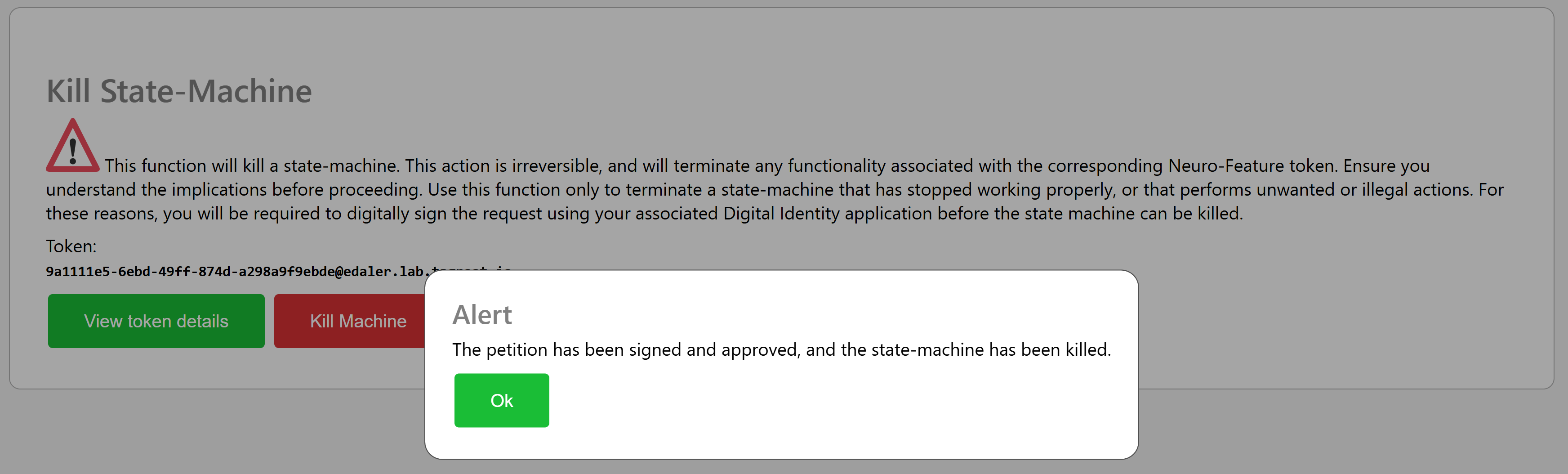
Take time to read through the purpose of the signature. If you agree, sign the petition, and the state-machine will be killed:
Embedding PDF Documents in Markdown via URL
As mentioned in a previous article, PDF documents can be embedded into Markdown. You can now also embed PDF documents, by simply using the URL, and embedding it into a multimedia construct in Markdown.
Example:

This results in:
Posts tagged #features
No more posts with the given tag could be found. You can go back to the main view by selecting Home in the menu above.